SSO with Azure
IndiCater should be set up as an enterprise application in Azure AD.
You will need two enterprise applications set up. One for live and one for testing the integration. Both applications should be configured to use SAML.
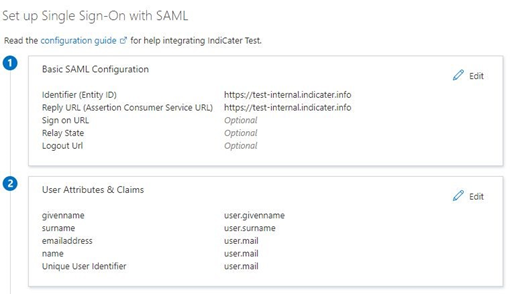
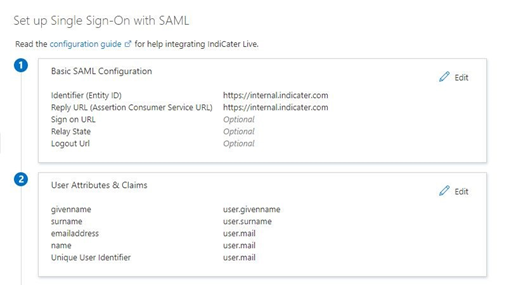
Basic SAML configuration
The Identifier and Reply Url are used to help with co-ordination of the SSO process. For IndiCaters purpose, they should normally be the same.
The reply URL dictates where a successful authentication attempt will be redirected to.
Identifier
Reply Url
Both the identifier and the Reply Url should be set to default.
User Attributes & Claims
Claims are used by IndiCater to match the successful authentication to a user in IndiCaters system. They are also used with the just in time user account creation or hospitality to populate new user accounts with a users details.
IndiCater primarily uses the name claim, so please ensure this is populated with the email that the user will using SSO with.
There are three types of user in IndiCater. External (Hospitality), HeadOffice, and Outlet. The matrix below shows which claims are required for each type of user. External users will be created by default if no additional claims are added to the default ones provided by Azure and a Hospitality outlet is present.
If claims are missing, or a hospitality outlet is not present when using the default Azure claims, then a 401 page will be shown to users trying to access the system.
Each time the user logs in, their claims are rechecked. If there is a discrepancy, it is changed to match the claims. Therefore outlets and roles can not be assigned within the system itself as they will be overridden on the next login by the values in the claims.
If the usertype claim is changed, then previous user account is archived and a new account created for them with the new user type.
Claim | Value | Required for Hospitality | Required | Required for Outlet | Default | Notes |
|---|---|---|---|---|---|---|
nameidentifier | Users Email Address | ✅ | ✅ | ✅ | ||
name | Users Email Address | ✅ | ✅ | ✅ | ||
emailaddress | Users Email Address | ✅ | ✅ | ✅ | ||
givenname | Users First Name | ✅ | ✅ | ✅ | ||
surname | Users Last Name | ✅ | ✅ | ✅ | ||
company | The company id the user should have access to | ❌ | ❌ | ❌ | 1 | Can be omitted if you only have one company set up in IndiCater |
usertype | HeadOffice or Outlet | ❌ | ✅ | ✅ | External | |
| outlets | A comma seperated list of outlet ids the user should have access to. | ❌ | ❌ | ✅ | Can be omitted for headoffice users. The first outlet in the list will be the default outlet for the user and the one they are logged into on sign in. | |
| roles | A comma seperated list of role ids the user should be assigned. | ❌ | ❌ | ❌ | Default Role | Can be omitted to assign user to the default role for their user type |
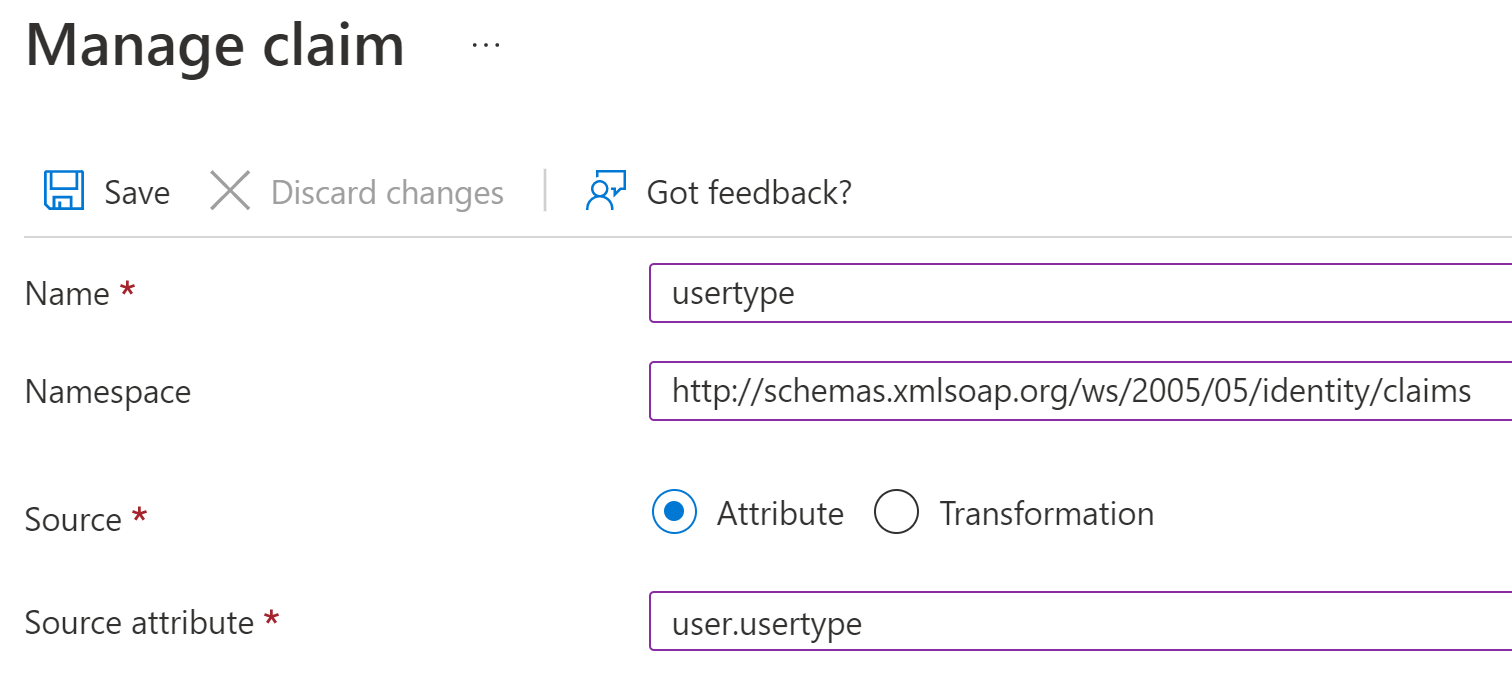
Creating a new claim
When creating a new claim, the namespace should be http://schemas.xmlsoap.org/ws/2005/05/identity/claims
The source attribute should be the source of the claims value in Azure AD
Example Claim Setups
External
| Claim | Value |
|---|---|
| nameidentifier | test.user@indicater.com |
| name | test.user@indicater.com |
| emailaddress | test.user@indicater.com |
| givenname | Test |
| surname | User |
Headoffice
| Claim | Value |
|---|---|
| nameidentifier | test.user@indicater.com |
name | test.user@indicater.com |
| emailaddress | test.user@indicater.com |
| givenname | Test |
| surname | User |
| usertype | HeadOffice |
Outlet
| Claim | Value |
|---|---|
| nameidentity | test.user@indicater.com |
| name | test.user@indicater.com |
| emailaddress | test.user@indicater.com |
| givenname | Test |
| surname | User |
| usertype | Outlet |
| Outlets | 5,7,9 |
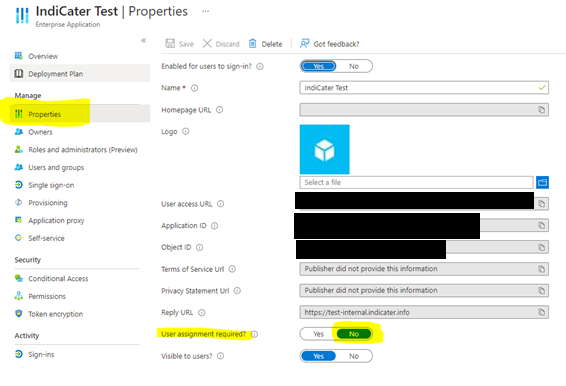
User assignment
If you are not assigning users specifically to the enterprise application, please make sure that ‘user assignment required’ field is set to ‘no’ otherwise users won’t be able to use the application. This field can be found by navigating to the enterprise application in Azure and should be under the settings blade.
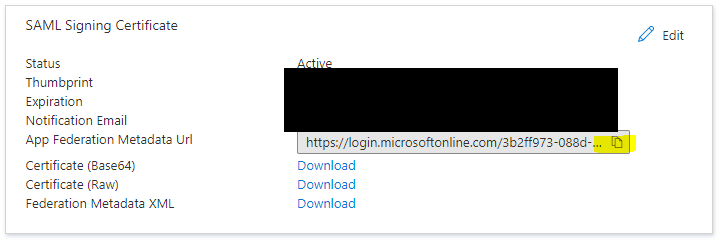
App Federation MetaData URLs
Once the two Enterprise applications have been set up, if you return the Federation Metadata URL for each, the SSO integration can be set up in IndiCater.
Example Configuration Test
Example Configuration Live
Updating Certificates
The SAML certificates generated by Azure expire every so often. You should be notified in advance of this happening. To ensure continued access to IndiCater, you must renew the certificate. We recommend you do this in advance of the expiry so that there is an overlap period that will allow you to continue using the existing certificate if any issues are encountered. These changes should be made out-side of peak use hours for your users.
To update your certificate
- Log into your Azure Portal
- Navigate to the Enterprise Application you have set up for IndiCater
- Navigate to Manage > Single Sign-on in the navigation bar on the left
You should end up at a page like this
In the SAML certificates section, click the edit button in the top right. This should bring out a popup window that shows your current active SAML certificate.
Click on the New Certificate button, then hit save. This should add a second certificate to the list.
You now need to make the new certificate active. To do this, click the three dot's next to the new certificate and then select "Make certificate active" and then confirm on the pop-up that appears.
Your new certificate is now Active.
Confirm that users can still log in.
After a few days and you are happy it's working, you can delete the old in-active certificate.